Create SPTrustedToken
Create SPTrustedToken
This section is quite important. Please make sure that this step runs successfully.
Use the following PowerShell code available at https://msdn.microsoft.com/en-us/library/office/dn579380.aspx#SingleAppScript or at the bottom of this page.
After that, run the script with your parameters, e.g.:
./HighTrustConfig-ForSingleApp.ps1 –CertPath "C:\Install\MeetingManager.cer" –CertName "MeetingManager" –SPAppClientID "dcc8d3d7-50d9-4cff-b594-5c80f756c473" –TokenIssuerFriendlyName "MeetingManager"
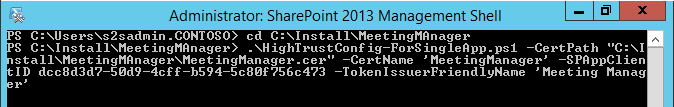
Parameters:
- CertPath: Full path to our public certificate (.cer) including file name which will be used for the Server2Server Trust.
- CertName: Common Name of the certificate used
- SPAppClientID: ClientID / App ID you've generated before
- TokenIssuerFriendlyName: Can be anything to help you identify that this trust belongs to Meeting Manager, e.g. Meeting Manager
Afterwards run "iisreset /noforce" which will restart SharePoint and all application pools. If you don't do this, you need to wait 24 hours in order that the trust will be enabled.
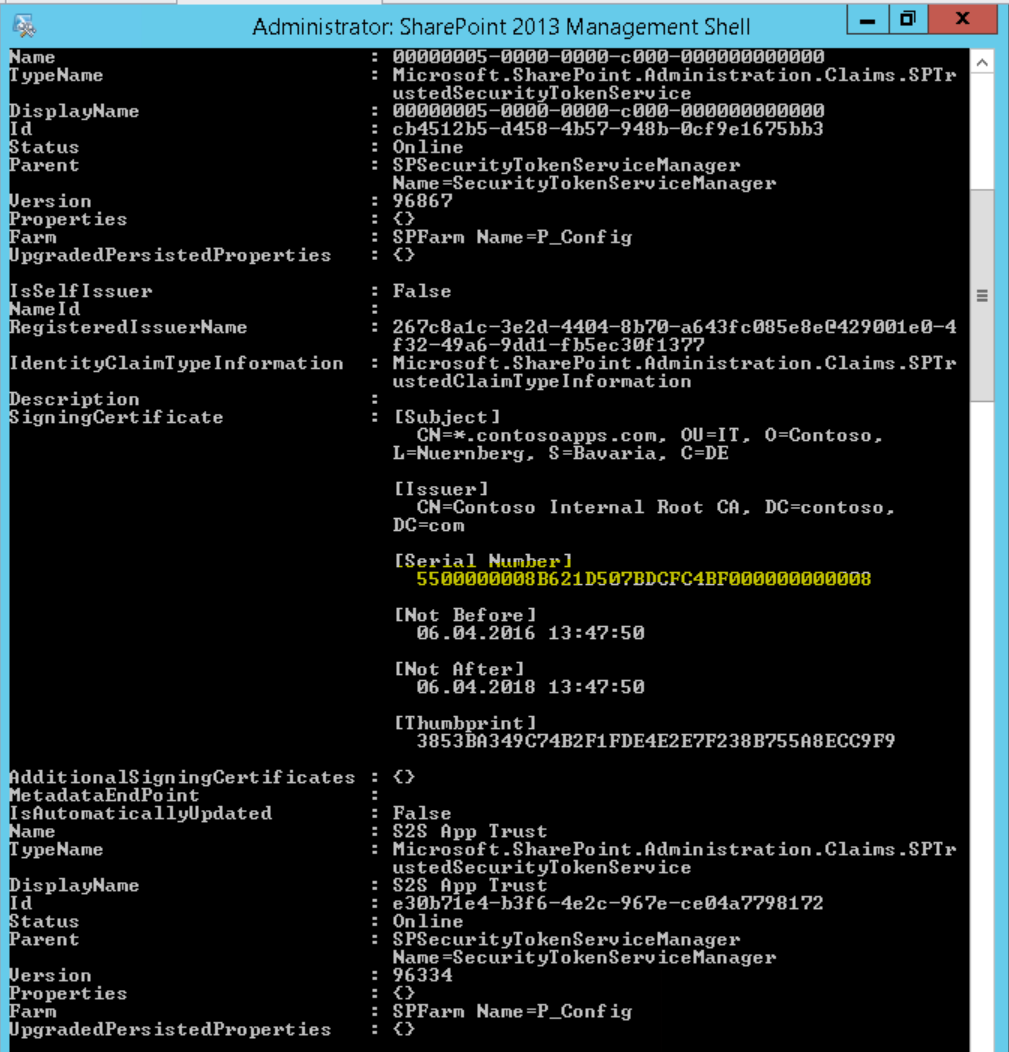
There will be a output, make sure you remember the Serial Number of the certificate (Note: This screenshot shows a different certificate as in the previous example):
HighTrustConfig-ForSingleApp.ps1
Save the following script as HighTrustConfig-ForSingleApp.ps1
param(
[Parameter(Mandatory)][String] $CertPath = $(throw "Usage: HighTrustConfig-ForSingleApp.ps1 -CertPath <full path to .cer file> -CertName <name of certificate> [-SPAppClientID <client ID of SharePoint add-in>] [-TokenIssuerFriendlyName <friendly name>]"),
[Parameter(Mandatory)][String] $CertName,
[Parameter(Mandatory)][String] $SPAppClientID,
[Parameter()][String] $TokenIssuerFriendlyName
)
# Stop if there's an error
$ErrorActionPreference = "Stop"
# Ensure friendly name is short enough
if ($TokenIssuerFriendlyName.Length -gt 50)
{
throw "-TokenIssuerFriendlyName must be unique name of no more than 50 characters."
}
# Get the certificate
$certificate = New-Object System.Security.Cryptography.X509Certificates.X509Certificate2($CertPath)
# Make the certificate a trusted root authority in SharePoint
New-SPTrustedRootAuthority -Name $CertName -Certificate $certificate
# Get the GUID of the authentication realm
$realm = Get-SPAuthenticationRealm
# Must use the client ID as the specific issuer ID. Must be lower-case!
$specificIssuerId = New-Object System.String($SPAppClientID).ToLower()
# Create full issuer ID in the required format
$fullIssuerIdentifier = $specificIssuerId + '@' + $realm
# Create issuer name
if ($TokenIssuerFriendlyName.Length -ne 0)
{
$tokenIssuerName = $TokenIssuerFriendlyName
}
else
{
$tokenIssuerName = $specificIssuerId
}
# Register the token issuer
New-SPTrustedSecurityTokenIssuer -Name $tokenIssuerName -Certificate $certificate -RegisteredIssuerName $fullIssuerIdentifier